With the exponential increase of the data rate in high-speed channels, their evaluation using an eye diagram simulation has become more cumbersome. This task is especially challenging for non-LTI systems, where statistical methods are not applicable and a long transient simulation with a random bit pattern is necessary. Therefore, we propose a machine learning approach based on Bayesian Optimization that creates an optimized bit pattern to maximize the ISI, resulting in faster convergence of eye diagram analysis. In addition, crosstalk, random noise, random jitter, and other types of interference can be added to the analysis. Numerical results demonstrate up to 14x speedup and more accurate results compared to the conventional eye diagram analysis.
Performance of high-speed Serializer/deserializer (SerDes) channels is often evaluated using an eye diagram. The conventional eye diagram is simulated with a lengthy transient simulation and a random bit pattern source (i.e., transient eye). However, for modern channels where the bit error rate (BER) is required to be 10‐12 or less, the simulation would be very time-consuming. Therefore, we propose taking advantage of modern machine learning techniques to generate an optimized bit pattern and use it in place of the random bit pattern, where the optimized bit pattern is significantly shorter. The bit pattern is optimized to maximize the inter-symbol interference (ISI), which refers to interference of a single bit response with neighboring symbols.1 Since ISI can span over many unit intervals (UIs) for modern channels, many combinations of this effect can exist; therefore, a significantly long random transient simulation would be necessary to capture the correct eye opening. However, by optimizing the bit pattern to converge to the most challenging waveforms, the eye opening is found with a significantly shorter transient simulation. Figure 1 illustrates the general topology of a PCIe link, which is an example of modern SerDes channels.

Figure 1. PCle topology
Statistical eye diagrams have been developed to avoid expensive transient simulation. This includes Peak Distortion Analysis2 and StatEye.3 However, unlike the proposed approach, they are only applicable to linear time-invariant (LTI) systems. Furthermore, parametric surrogate models of high-speed channels have been proposed in the literature.4,5 However, these methods require a dataset of existing designs with variations of design parameters for training. In addition, training a surrogate model can limit accuracy. In contrast, the proposed approach in this article does not require an initial dataset and the optimization is performed with adaptive dynamic sampling. Additionally, the proposed approach works with accurate short time domain simulations, and it does not suffer from the loss of accuracy caused by surrogate models. A survey of other eye estimation methods and their respective limitations is provided by Dolatsara.6
Recently, a novel method known as the Worst-Case Eye analysis was introduced.7 This methodology is designed to alter the bit sequence in a way that intensifies ISI and yields eye height, eye width, and the contour of the eye opening. In the present study, we expand upon this methodology. The significant enhancement involves producing the worst-case bit pattern rather than the eye metrics. Leveraging this progression, we have been able to perform a faster and more accurate eye diagram simulation compared to the traditional transient eye. It also has enabled us to incorporate various types of noise and jitter into the worst-case eye diagram. Additional steps are also taken to improve the optimization in Dolatsara, et al.7, including a new way of handling discrete variables, avoiding repeated samples, and the normalization of objective functions. The proposed approach is henceforth termed the Worst-Case Bit-Pattern Generator (WCBPG). WCBPG has been recently released with Keysight Advanced Design System (ADS) 2024 Update 1.0.8
Background Review
In this section, Gray code mapping and Bayesian optimization (BO), which were used in the development of WCBPG, are reviewed.
Gray Code Mapping
The reflected binary code, or the Gray code, is a reordering of the binary numbers so that each two subsequent numbers only differ in a single binary digit. For instance, in a two-bit system, the binary numbers are {00, 01, 10, 11}. Gray code maps this sequence to {00, 01, 11, 10}9. Gray code is used in WCBPG to map the possible bit patterns to a space that is easier to optimize. This is discussed further later in this article.
Bayesian Optimization
BO is a dynamic optimization technique in machine learning applicable to nonlinear and nonconvex functions. It is especially effective for optimization of functions that are costly to evaluate, thanks to its economical use of samples and fast convergence. It is an iterative algorithm based on the Bayes theorem.10 Figure 2 illustrates three iterations of BO for maximization of a one-dimensional (1D) test function. f(x) represents the unknown objective function, which has been sampled at D1:t, with t being the current iteration. Furthermore, Gaussian Process (GP) is used for modeling f(x), which is shown by N(μt (x),σt2 (x)) representing a normal distribution for f(x) at every point, with mean equal to μt and variance equal to σt2. It represents where the model expects f(x) to appear. Moreover, the acquisition function, u(μt (x),σt (x)), is used to balance exploration and exploitation and find the next sample for evaluation, which is most likely to converge toward the global maximum. Note that u(μt (x),σt (x)) is plotted on a different scale shown on the right side of each plot. It illustrates a given score for each possible future sample. The maximum of this analytical function is marked and shows the next sampling point, xt+1. The algorithm repeats until reaching a preset limit and updates GP based on the new observations. Finally, it reports the maximum found sample. For mathematical details including the Gaussian Process and the acquisition function, see Brochu, et al.10
 Figure 2. First three iterations of BO on a 1D test function.
Figure 2. First three iterations of BO on a 1D test function.
The Proposed Worst-Case Bit-Pattern Generator (WCBPG)
Jitter and noise are affected by the memory effect and the bit pattern sequence in high-speed channels. We show a partial bit pattern surrounding the current symbol (i.e., current bit) as: 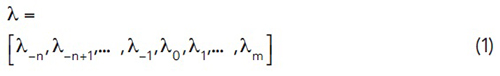
where λ0 is the current transmitted symbol, λ‐1 to λ‐n are the previous symbols with non-negligible post-cursors in ISI, and λ1 to λm are the future bits causing the non-negligible pre-cursors in ISI. WCBPG optimizes λ to achieve the worst-case eye (WCE) opening. WCE is defined as the eye with the smallest eye height (EH) and eye width (EW), since these two measures are often used as the major metrics to compare the eye diagrams. Currently, the proposed approach supports the non-return-to-zero (NRZ) signal; however, the following methodology can be easily extended to PAM-n. As shown in Figure 3, for the NRZ signal, EH is the difference between the lowest received high symbol and the highest received low symbol.

Figure 3. EH and EW on a sample eye diagram and their calculation using lowest high, highest low, and leftmost and rightmost zero-crossing points.
On the other hand, EW is UI minus the peak-to-peak jitter (PPJ), where PPJ is the difference between the rightmost zero-crossing and the leftmost zero-crossing, where zero-crossing is defined as the time point when a rising or falling edge passes through the threshold voltage differentiating the high and low logics. This breaks down finding the WCE into six smaller optimization problems, which are finding the lowest high voltage (VLH), highest low voltage (VHL), rightmost rising edge zero-crossing time (tRR), rightmost falling edge zero-crossing time (tRF), leftmost rising edge zero-crossing time (tLF), and leftmost falling edge zero-crossing time (tLF) as a function of λ, which we call the worst-case points.
The optimization space in the problems above is high-dimensional due to the large n in modern channels. It is also discrete and sparse since λi can only take zero or one values. This results in challenging optimization problems. Therefore, we use our knowledge of high-speed channels to simplify the optimization. For the problems considered in this article, m is fixed at 1 since further pre-cursors are negligible. Moreover, [λ‐1,λ0,λ1] are set intuitively for each optimization problem based on the behavior common to high-speed channels. For instance, for the lowest high, these three symbols are always set to [0,1,0]. Furthermore, a decimal number equivalent to [λ‐n,λ‐n+1,…,λ‐2] is generated, where λ‐n is the least significant bit (LSB), and λ‐2 is the most significant bit (MSB). We call this number the index of each possible bit pattern. The optimization is now converted to a 1D problem where the index number corresponding to the worst-case points needs to be found. Note that for ISI, λ‐n is the least effective symbol since it is the furthest from the current symbol. Therefore, by choosing λ‐n as the LSB, the variation in ISI for adjacent bit patterns is relatively gradual. However, adjacent binary digits can be significantly different or even completely opposite in the binary domain. Therefore, we use the Gray code mapping to reorder the bit pattern indices and create smoother objective functions. In conclusion, the optimizer needs to solve the following optimization problems:
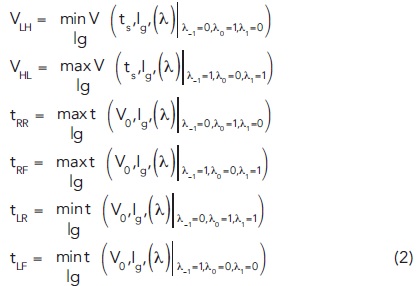
where V(ts,Ig (λ)|λ‐1 =.,λ0=.,λ1=.) is the output voltage at ts, when the bit pattern corresponds to the Gray code index Ig, and t(V0,Ig (λ)|λ‐1=.,λ0=.,λ1=.) is the time when the desired rising/falling edge passes the threshold voltage V0, when the bit pattern corresponds to the Gray code index Ig. PPJ is calculated as max(tRR,tRF ) ‐ min(tLR,tLF ). Figure 4 illustrates a snapshot of optimization of VHL in a test case, in the same format as Figure 2.

Figure 4. Snapshot of an example for WCBPG while optimizing VHL.
In this work, finding a maximum with BO is implemented in C++, and finding a minimum is achieved by finding the maximum of negative of the objective function. The following steps are taken to improve performance of BO compared to Dolatsara, et al.7 Conventional BO is designed for optimization of continuous variables. In Dolatsara, et al.7 BO samples were simply rounded to the nearest integer; however, this can degrade the performance. In WCBPG, BO is adapted by modifying the sample space of the acquisition functions. In this approach, unlike the conventional BO, the acquisition function is only evaluated at a bag of random integer samples. Then, the sample with the highest score is selected to be evaluated at the next iteration to update the Gaussian Process model. To avoid reselecting the same samples, at the beginning of each iteration, we remove the samples that we have evaluated so far from the bag of samples given to the acquisition function. Therefore, we do not consider them when looking for the next sample. Furthermore, V0 and ts in Equation (2) are calculated as: 

where Vmax and Vmin are the maximum and minimum received voltages, respectively. Moreover, hyperparameters of BO can differ from one example to another. To avoid resetting these parameters for each test case, we normalize the objective functions in Equation (2), using Vmax and Vmin for voltage functions and the unit interval for time functions. Next, the bit patterns equivalent to the indices found in Equation (2) are constructed. After adding some zero-padding, these bit patterns are concatenated and written into a file; then, the result is fed to a transmitter and used for eye diagram simulation. Finally, random noise and jitter and other types of distortion are added to the transmitter’s output as usual.
Numerical Examples
Example 1
To evaluate performance of WCBPG, the channels shown in Figure 5, which are taken from a DDR4 DIMM system, are considered. It includes 11 coupled channels, input sources, and 50 Ω terminations. It operates at 3.2 Gbps. Vhigh and Vlow of the transmitter are set to 1.2 V and 0.0 V, respectively. Initially, all the sources transmit random patterns.
Figure 5. The high-speed channel considered in example 1.
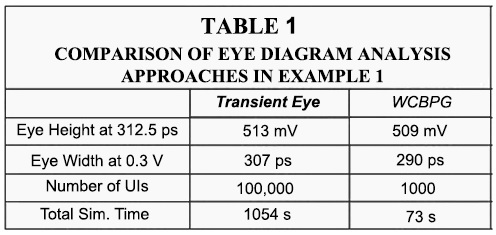
We focus on the analysis of the fourth channel from the top. The eye diagram is measured before the termination. Figure 6a illustrates the conventional eye diagram of this channel, which is performed with 100,000 random bits; its specific metrics are provided in Table 1.

Figure 6. Eye diagram at the output of example 1, using a) conventional transient eye and b) the proposed WCBPG.
Next, we utilize the proposed WCBPG to create the worst-case bit pattern for this channel. n in Equation (1) is set to 13, based on the single bit response of this channel in absence of crosstalk as shown in Figure 7; however, crosstalk is present when the bit pattern is being generated. Moreover, the number of iterations for optimizing each objective function in Equation (2) is set to 25. We use the bit pattern generated by WCBPG to run a transient simulation for the length of 1000 UIs. Therefore, we run through the generated bit pattern multiple times, which is done so for practical reasons.

Figure 7. Single bit response of the channel in example 1.
The resulting eye diagram analysis results are presented in Figure 6b as well as Table 1, which shows a smaller eye opening compared to the transient eye. Note that in this context, smaller is more accurate because the eye diagram in Figure 6b is actually derived from a transient simulation with an optimized bit pattern. The total simulation time of this approach is 73 seconds, which includes the BO and generation of the worst-case bit pattern. Therefore, it provides an increase in speed of roughly 14x compared to the conventional eye diagram analysis, while the results are considerably more accurate.
Example 2
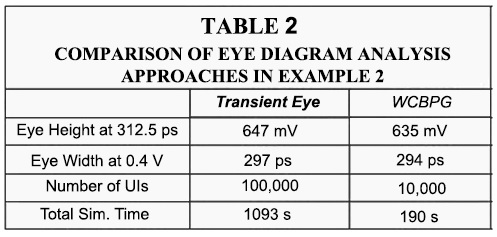
In this example, we have modified the system in example 1 by creating a differential channel using the fourth and fifth channels from the top and measuring the differential corresponding output, as shown in Figure 8. In addition, random jitter (RJ) and sinusoidal periodic jitter (PJ) have been added to this channel’s transmitter. Standard deviation of RJ is set to 1 ps. PJ’s amplitude and frequency are 2 ps and 100 MHz, respectively. The rest of the parameters stay the same. The conventional eye diagram using 100,000 random bits is illustrated in Figure 9a. In addition, the eye metrics are summarized in Table 2.

Figure 8. The high-speed channel considered in example 2.
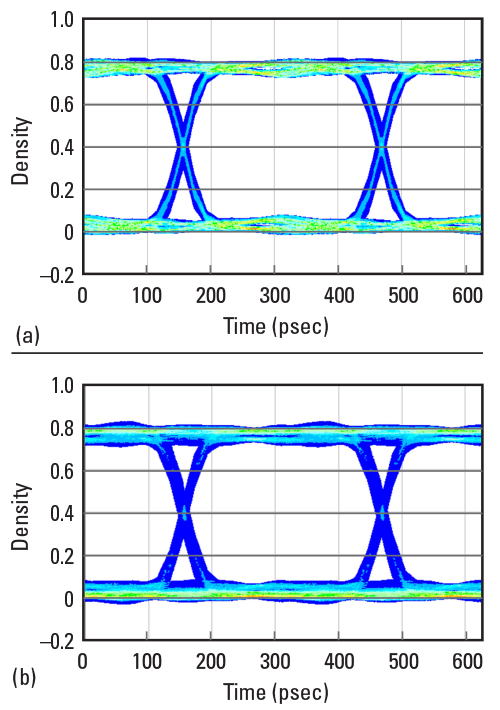 Figure 9. Eye diagrams at the output of example 2, using a) conventional transient eye and b) the proposed WCBPG.
Figure 9. Eye diagrams at the output of example 2, using a) conventional transient eye and b) the proposed WCBPG.
For WCBPG, n in Equation (1) is set to 16 based on the single bit response of this channel in absence of crosstalk, as shown in Figure 10; however, crosstalk is present when the bit pattern is being generated. Moreover, the number of iterations for optimization of each objective function in Equation (2) is set to 30. The worst-case bit pattern is generated with no RJ and PJ to maximize ISI. Next, RJ and PJ are turned on, and a transient simulation for the length of 10,000 UIs is performed using the created bit pattern. We have increased the length of this simulation to 10,000 UIs because it includes RJ and PJ. Since WCBPG does not optimize for RJ and PJ, we need to increase the length of the simulation to observe their effects; however, the total simulation time would be much shorter than the entirely random transient eye.
Figure 10. Single bit response of the channel in example 2.
The resulting eye diagram analysis results are presented in Figure 9b and Table 2, showing a smaller eye opening than the transient eye. As discussed before, this shows the WCBPG results in a more accurate eye diagram, even in the presence of RJ and PJ. In addition, the results are generated 5.75x faster than the transient eye.
Conclusion
In this article, WCBPG is introduced to create a bit pattern for faster eye diagram analysis of high-speed channels. The pattern generated by WCBPG utilizes Bayesian Optimization to maximize ISI; moreover, it takes advantage of the Gray code mapping to create smoother objective functions. Numerical examples show that the proposed approach demonstrates a superior performance compared to conventional eye analysis, even in the presence of crosstalk, RJ, and PJ.
REFERENCES
- M. P. Li, Jitter, Noise, and Signal Integrity at High-Speed, Upper Saddle River, NJ, Prentice Hall, 2007.
- B. K. Casper, M. Haycock, and R. Mooney, “An Accurate and Efficient Analysis Method for Multi-Gb/s Chip-to-chip Signaling Schemes,” in IEEE Symp. Very Large Scale Integr. (VLSI) Circuits, 2002.
- A. Sanders, M. Resoo, and D. Ambrosia, “Channel Compliance Testing Using Novel Statistical Eye Methodology,” DesignCon, 2004.
- T. Lu, J. Sun, K. Wu, and Z. Yang, “High-Speed Channel Modeling With Machine Learning Methods for Signal Integrity Analysis,” IEEE Transactions on Electromagnetic Compatibility, Vol. 60, No. 6, 2018, pp. 1957-1964.
- Y. Choi, P. Kashyap, W. Sun, M. S. Chughtai, C. Cheng, and P. Franzon, “Data-driven PAM4 SerDes Modeling with Generative Adversarial Network,” DesignCon, 2023.
- M. Ahadi Dolatsara, “High-Speed Channel Analysis and Disign Using Polynomial Chaos Theory and Machine Learning,” Doctoral dissertation, Georgia Institute of Technology, 2021, pp. 8–14.
- M. Ahadi Dolatsara, J. A. Hejase, W. D. Becker, J. Kim, S. K. Lim, and M. Swaminathan, “Worst-case Eye Analysis of High-speed Channels based on Bayesian Optimization,” IEEE Transactions on Electromagnetic Compatibility, Vol. 63, No. 1, Feb. 2021,pp. 246–-258.
- “PathWave Advanced Design System (ADS),” Keysight Technologies, Web: https://www.keysight.com/us/en/products/software/pathwave-design-software/pathwave-advanced-design-system.html. [Accessed 3 November 2023].
- H. S. Wilf, “Combinatorial Algorithms: An Update,” Philadelphia, PA, SIAM, 1989.
- E. Brochu, V. M. Cora, and N. de Freitas, “A Tutorial on Bayesian Optimization of Expensive Cost Functions, with Application to Active User Modeling and Hierarchical Reinforcement Learning,” arXiv:1012.2599, 2010.

